 Product
Product FLProtection®
FLProtection® Product
Product FLProtection®
FLProtection®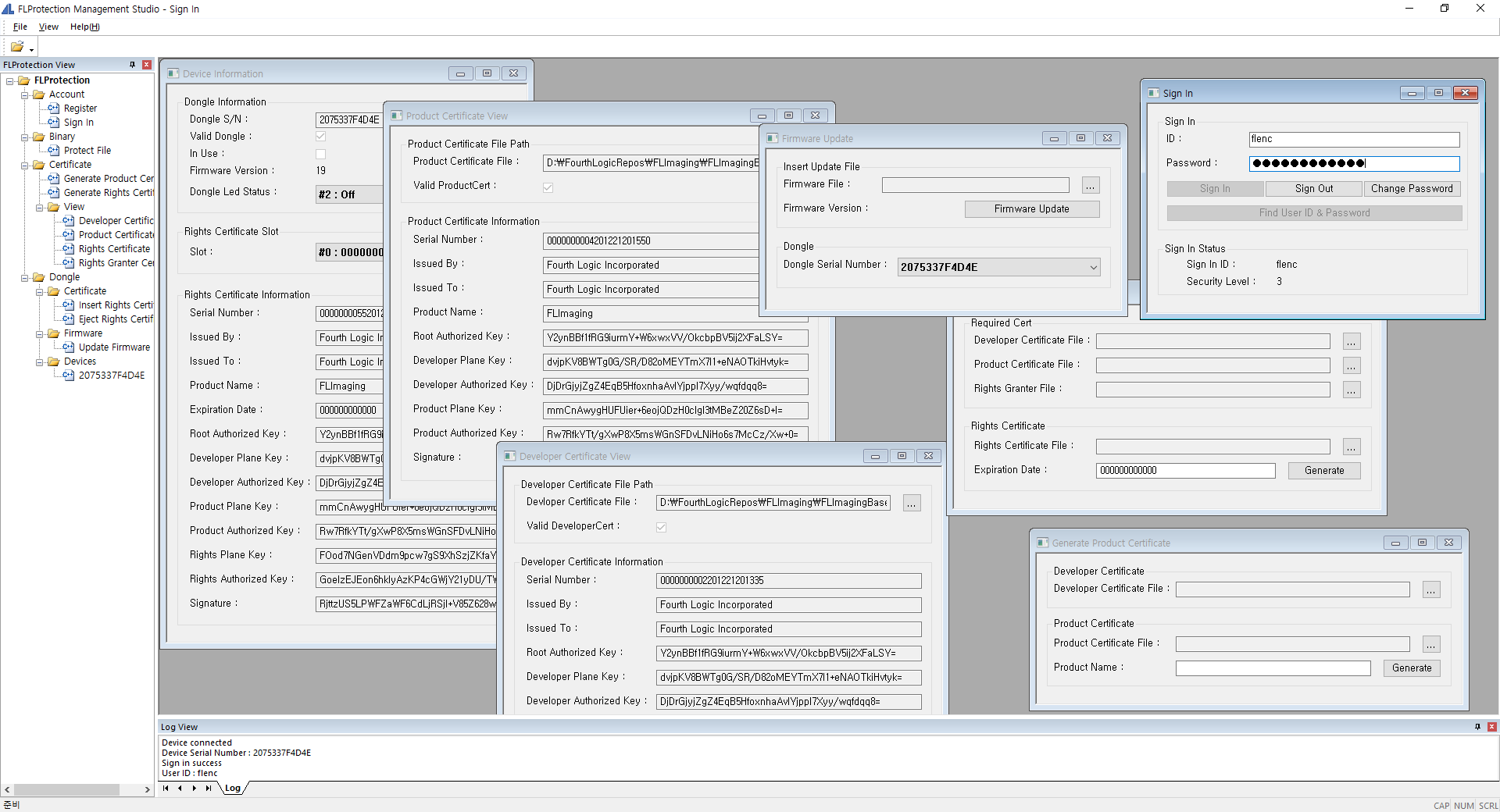
FLProtection® is a certificate-based software license platform, supporting USB dongle and network certification all at once.
FLProtection® prevents your software from illegal, unlicensed usage.
It supports both hardware(USB dongle) and software(network)-based security, each strictly discriminating the authorized user based on the rights certification system.
Features
Full encryption of data using RSA2048 and AES256
Certificate-based software user authorization
Dualization of the certification media(Applied for patent)
Supporting numerous executable files
Powerful anti-debugging
USB hardware protection
On-line USB dongle firmware update
Security acquired from total encryption of data using RSA2048 and AES256
- RSA2048 : Applied during the exchange of random generated AES256 keys
- AES256 : Applied during the communication of data with USB dongle or server, using the exchanged keys
Certificate-based software user authorization
- Encryption of the executable file / Decryption on software runtime(Applied for patent)(*)
- Encrypted distribution of the executable file using the product certificate
- Can execute after the decryption of the file is done by the authority certificate
- Dualization of the product and authority certificate, allows separate certifications. While the product is encrypted with a single certificate, the execution and decryption of the users are done by multiple authority certificates of each. (Applied for patent)
- Program cannot be executed just by disarming the security solution, unless they crack the AES256 system
Dualization of the certification media
- On-line : Network certification
- Off-line : Hardware certification using USB dongle
Supporting numerous executable binary files
- Native
- Windows executables(EXE)
- Dynamic libraries(DLL, COM etc.)
- Managed
- .NET
- Java
Powerful anti-debugging
- Blocks debugging executable files
- Blocks debugging dynamic libraries
- The software that imports the protected library is still available of debugging.
- But, debugging is blocked when debug attempt on the protected library is detected.
- Other security solutions blocks debugging the total software, making it inconvenient for developers.
- Memory manipulation defense
- Prevents cracking with memory dump
- Encrypted dump file is always creatable
- Everyone can use memory dump
- Only the ones with the developer certificate can read the original code
- Cracking methods such as DLL injections, are blocked at source.
USB hardware protection
- Hardware is blocked at source from debugging.
- Even when the flash memory data is extracted, safety guaranteed because all the data is saved after the encryption.
On-line USB dongle firmware update(Applied for patent)
- One-click update is available when the new firmware release is distributed
- No additional hardware required
Certificate types
Root certificate
- Used in validation certification
- Encrypted and saved at server or USB dongle
Developer certificate
- The certificate that the company or developer uses
- Issued by Fourth Logic Inc. after the recipient / business identification, and the root certification - Used in creating product certificates, which identifies developers and prevents creating counterfeit certificates
Product certificate
- Issued by the company or developer after the developer certification
- Used in protecting the product, by encrypting the executable file with the product certificate.
Rights certificate
- Issued by the company or developer after all of the developer, product, rights granter certification is done. - The actual software usage license
Rights Granter certificate
- Issued by Fourth Logic Inc. after root certification
- The certificate that the company or developer requires to issue the rights certificate